Even though there has been extensive research on DDoS attacks, they remain a challenge today. Since it does not wait for a specific network configuration or network state to attack, DDoS attacks remain powerful to date. With Machine learning, the main agents of DDoS attacks have become stealthier, sophisticated, and intelligent. Bots can now adapt and evade detection mechanisms while continuously harming your server. Cybercriminals develop and release malicious botnets to the internet having various intentions. The denial of certain services is a key intention.
What is a DDoS attack?
Distributed Denial of Service (DDoS) is the malicious attempt by cybercriminals to overwhelm a network by flooding it with superfluous traffic. DDoS attacks have the effect of degrading network performance or service outage of critical infrastructures. The motivation for this form of attack is not financial. So, why then would a person perform a DDoS attack on your website or server? Below are some reasons why an attacker may want to perform a DDoS attack on your server or website.
Motivation for DDoS attacks
Nature of your content (Ideologies)
When a cybercriminal has a different ideology with your content, they can launch botnets to ensure that the content is not accessible. Successful DDoS puts your content out of circulation. While the attacker’s intentions have been fulfilled, your users are left with problems whenever they want to access the information. This makes you lose the revenue you might have been making from the website. Because your site returns a 502 error for some time, its rankings on the Search Engine Results Page may drop.
Political motivation (Hacktivism)
Nowadays, there has been an increase in politically motivated DDoS attacks. Amongst other cyberthreats, DDoS has been the common tool for disrupting the political process. Cybercriminals have been targeting websites for political parties, organizations, or candidates that advance a political cause that differs from the attackers.
Competition
Business competitors can use nasty tricks like DDoS attacks on your website to gain an edge over your products. Ideally, they can legally outperform you by improving their SEO, content, and conversion rate. After a DDoS, the competitors can make a killing by using your business name as a keyword for running ads.
Anatomy of a DDoS Attack
The attacker writes the code for the bot and networks them to build a botnet. The infected botnets are then distributed through email, social media, and clickable links to various targets. Once infected, the cybercriminal can control the target website or server remotely without the owner knowing. The attacker then launches the attack on the target.
The botnets are used to generate superfluous traffic and flood the site or server with it. This traffic overwhelms the web server, thereby degrading service performance or causing a service outage. The traffic floods can be done by amplifying requests or sending bulk random data to use up the victim’s bandwidth. Effectively, this downs the services of a website. To understand how to prevent DDoS attacks, you need to acquaint yourself with its different types.
Types of DDoS attacks
Volumetric attacks
They are the most common type of DDoS attack. The attacker attempts to utilize the network service’s bandwidth or the bandwidth between the more extensive internet and the target network service. An example of a Volumetric attack is the Domain Name System (DNS). Cybercriminals spoof the address of the target. They then perform a DNS lookup to an open DNS server using the spoofed address. The attacker then sends the DNS record response to the target. Therefore, the target receives an amplified version of the attacker’s query.
Application layer attacks
In this type of attack, the cybercriminal sends requests that seem innocent and legitimate with the intention of crashing the webserver. It can be accomplished by Slowloris, where a botnet sends a bulk of HTTP headers to the target without completing the request. By keeping these false connections open, an overflow of the maximum current connection pool occurs. Therefore, denial of legitimate clients’ incoming requests happens. Other forms of layer seven attacks are NTP Amplification, zero-day DDoS attacks, and application attacks.
Protocol attacks
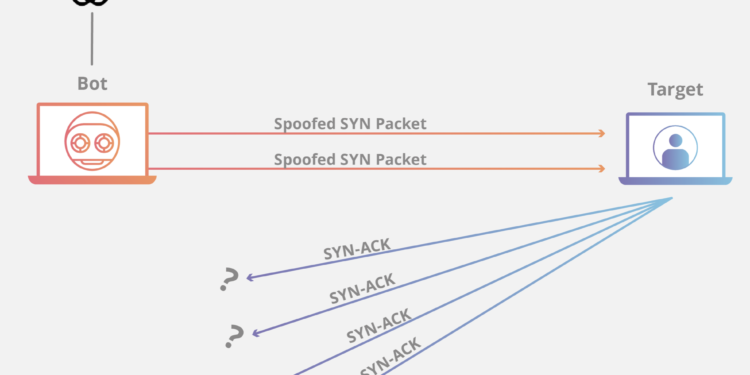
These attacks work by exposing the vulnerabilities in layers 3 and 4 of the OSI protocol stack making the target inaccessible. They use up the total capacity of the web servers and other resources like firewalls. Examples of these attacks include SYN floods, DNS flooding, and ping of death. In SYN flooding, the botnets send TCP requests at a higher rate than the target can handle. This causes network saturation.
The other form of DDoS attack is the Fragmentation attack. Using the botnets, the attacker exploits the weaknesses in the datagram fragmentation process. During the reassembly stage of the IP datagram packets, the fake data packets are not reassembled; therefore, they overwhelm the server.
Signs of a DDoS attack
You need to check for the below signs if you think you’ve been a victim of a DDoS attack.
- Regular internet disconnection
- Difficulty and problems accessing websites
- If you are unable to access a specific website for a long time
- A large number of spam emails
- Slowed access of files both local and remote
How to Prevent DDoS Attacks
Rate limiting
To prevent DDoS attacks, you can limit the number of incoming requests to a server over a window of time. In combination with some other measures, rate limiting is effective in stopping DDoS attacks like SYN flooding.
Web Application Firewall (WAF)
When a web application firewall is placed between the internet and the origin server, it acts as a reverse proxy. It prevents a target server from getting various types of malicious traffic. Therefore, WAFs effectively impede layer seven attacks by filtering all requests based on a series of rules to identify DDoS tools. Effective WAFs can implement custom rules quickly while responding to an attack.
Differentiating the traffic
If you believe that your website is a victim of a DDoS attack, you need to assess the quality and source of the traffic. Using an anycast network will help you in scattering the abnormal traffic over a network of distributed servers. By doing this, you ensure better network manageability because the network absorbs the traffic.
Risk Assessment
Though impossible to avoid DDoS, you should routinely conduct audits and risk assessments on your web servers and network. This will help you know the most vulnerable parts of your network. Therefore, you can craft an effective strategy to lower the risk of DDoS attacks or reduce the damage and disruption when it arises.
Purchasing or Subscribing to a DDoS protection solution
DDoS solutions like DataDome help you defend and monitor your web server. Because the attacks are becoming more complex and sophisticated, individuals and companies require a solution that can help them deal with known attacks and Zero-day attacks. There are a few effective ways to protect from layer 7 DDoS attacks. It utilizes a combination of machine learning and artificial intelligence to detect bots and botnets in your networks within milliseconds. By real-time analysis of every request on a web server, it ensures that no attack reaches your servers. Because the DataDome solution is delivered as-a-service, no architectural changes or rerouting of DNS is needed. IT eliminates the dangers of a single point of failure.
Bottom Line
DDoS attacks are prevalent to date. They affect political sites, government sites, and cloud service providers. For varying reasons, attackers result in this illegal form to express displeasure, revolt, agitation, or ideologies. Therefore, it is essential to keep watch on various signs that your web server is compromised. Additionally, conducting a regular risk assessment on critical infrastructure can help you in mapping vulnerable segments. Purchase a DDoS protection software like DataDome to protect your online infrastructure against DDoS attacks and all other attacks emanating from bot and botnet activities.